How to install and active crowdsec in pangolin
Prerequisits: Succesful installation of pangolin + DNS entries
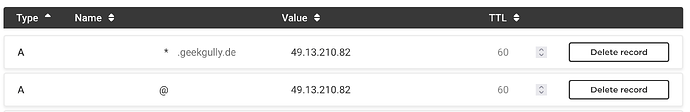
Domain and DNS entries:
For beginners: You should own a fresh domain name with no other A records than these 2, pointing to your VPS IP (example):
Succesful installation of pangolin
-
You should already have pangolin installed as written in the Docs.
-
And you should have gotten this message at the end of installation, like this:
Installation complete!
To complete the initial setup, please visit:
https://pangolin.geekgully.de/auth/initial-setup
Diesen Link aufrufen und admin account anlegen!
Web-Interface of pangolin
You sould have visited the Web-Interface of your pangolin instance at least once, you should have setup the organisation already. No need to have a site yet.
Installation of crowdsec
Installation procedures
Start the installer of pangolin again like this:
sudo ./installer
You should see the following text:
Welcome to the Pangolin installer!
This installer will help you set up Pangolin on your server.
Please make sure you have the following prerequisites:
- Open TCP ports 80 and 443 and UDP ports 51820 and 21820 on your VPS and firewall.
- Point your domain to the VPS IP with A records.
http://docs.fossorial.io/Getting%20Started/dns-networking
Lets get started!
Would you like to run Pangolin as Docker or Podman containers? (default: docker):
Here you respond with ENTER
You receive this text now:
Looks like you already installed, so I am going to do the setup…
=== CrowdSec Install === Would you like to install CrowdSec? (yes/no) (default: no):
Respond with YES
Next:
This installer constitutes a minimal viable CrowdSec deployment. CrowdSec will add extra complexity to your Pangolin installation and may not work to the best of its abilities out of the box. Users are expected to implement configuration adjustments on their own to achieve the best security posture. Consult the CrowdSec documentation for detailed configuration instructions. Are you willing to manage CrowdSec? (yes/no) (default: no):
Respond with YES
Next:
Detected values: Dashboard Domain: pangolin.geekgully.de Let’s Encrypt Email: mail@geekgully.de Badger Version: v1.2.0 Are these values correct? (yes/no) (default: yes):
Respond with YES if it’s correct
Next:
Installation complete!
To complete the initial setup, please visit:
https://pangolin.geekgully.de/auth/initial-setup
Now crowdsec is installed, congratulations!
crowdsec acitivation:
Execut these two commands now to activate crowdsec:
docker compose down
docker compose up -d
Is all working correctly?
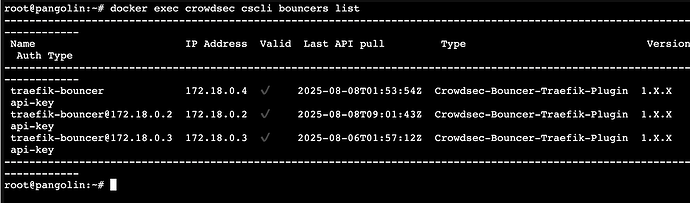
To see if crowdsec is working correctly, send this command:
docker exec crowdsec cscli bouncers list
When you see a text output like this, all is working well:
---------------------------------------------------------------------------------------------------------------
Name IP Address Valid Last API pull Type Version Auth Type
---------------------------------------------------------------------------------------------------------------
traefik-bouncer 172.18.0.4 ✔ 2025-08-05T13:55:54Z Crowdsec-Bouncer-Traefik-Plugin 1.X.X api-key
---------------------------------------------------------------------------------------------------------------
Crowdsec dashboard
If you already have a login to the crowdsec dashboard, you can add this crowdsec instance to the dashboard. If not, use the link to register first.
Add pangolin to your crowdsec dashboard
Show enrollment key
Klick in your crowdsec dashboard on the button “Enroll command”, you will see a window with a command like this:
sudo cscli console enroll -e context <MyEnrollemtKey>
Copy the part at the end, after “context”, which is marked MyEnrollmentKey
Enroll command
Now execute the following command in your ssh console on the VPS to add your pangolin instance with crowdsec to your dasboard, add the Key to the end of the command:
docker exec crowdsec cscli console enroll <MyEnrollmentKey>
crowdsec Dashboard
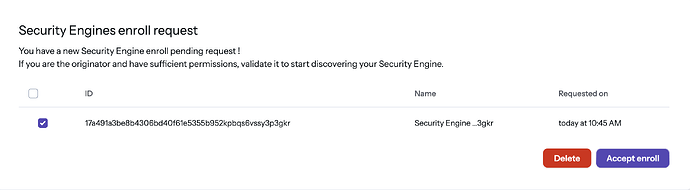
Switch to your crowdsec dashboard now, you will see a popup like this after a view moments:
Klick to accept it.
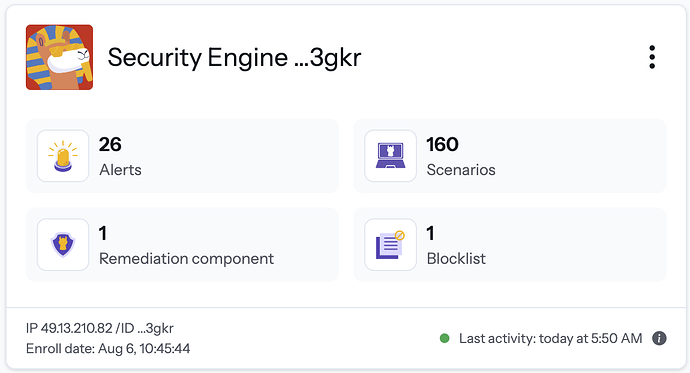
After a view seconds, you see your pangolin instance in the corwsec dashboard, like this:
Now you’re set and ready!
You have your pangolin instance with crowdsec added to the dashbord and you can watch which treads for your pangolin instance arise.
Note at the end:
@hhf.technoloy created a traefik dashboard to visualize what happends in you pangolin instance, I will write a guide for it later.