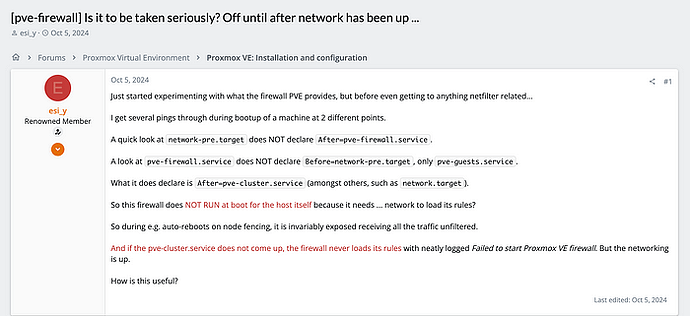
Proxmox Virtual Environment (PVE) is a powerful platform widely used for managing virtual machines and containers. One of its useful features is the built-in firewall, which allows users to configure rules for both the host and guests. However, while the Proxmox firewall offers a convenient layer of protection, it’s crucial not to rely on it as the sole line of defense, especially for the host zone.
A significant issue has been identified and tracked under Bug 5759, highlighting a vulnerability in how the Proxmox firewall operates during the system boot process. Specifically, the firewall does not apply any rules until the cluster service and network are fully initialized, leaving the host exposed without any firewall protection during that time. This is because the firewall requires access to its configuration files, which are typically stored on networked nodes, meaning that if the cluster service fails to start or encounters a delay, the firewall remains inactive. This gap leaves the host vulnerable to external threats until the configuration is loaded and the firewall becomes operational. It underscores the importance of not relying solely on the built-in Proxmox firewall for host security, as the host could be exposed during critical moments of the boot cycle, especially if the cluster does not properly initialize.
Understanding Proxmox Firewall and Host Zone
The Proxmox firewall is designed to protect both the virtual machines (guests) and the host server itself. In a clustered environment, the firewall rules are typically stored on a shared configuration file that is accessible by all nodes. These firewall rules control access to services running on the host and the virtual machines.
The host zone refers to the firewall rules that are applied specifically to the Proxmox host (the physical server running the virtual environment). While this feature can be beneficial, there are some significant concerns when relying solely on it for host protection.
The Risk of Firewall Delays During Boot-Up
One of the core issues with the Proxmox firewall is its dependency on the cluster services and the network. When a Proxmox server boots, the firewall rules are not applied immediately. This delay occurs because the firewall service requires the cluster to start and load its configuration before it can function.
In practical terms, this means that during the server’s boot-up process, the host is exposed without any firewall rules applied, leaving it vulnerable to potential attacks or unauthorized access. If the cluster services fail to start (either due to configuration issues or other network problems), the firewall rules for the host may never be loaded, leaving the host completely unprotected. While guests may not be able to start, the host itself is still exposed.
Key Limitations of Relying on Proxmox Firewall Alone
- Firewall Activation Dependent on Cluster Services: The Proxmox firewall relies on the availability of the cluster to load its configuration. If the cluster service fails to start, or if there is a problem with network connectivity, the firewall rules won’t be applied, leaving the host vulnerable. This can be a significant issue in both single-node and multi-node setups.
- Firewall Rules Not Applied During Boot: Even when the cluster services start as expected, the firewall rules are not applied immediately. There is a window of time during the boot-up process where the firewall is inactive, meaning that external threats could potentially access the system during this period.
- No Default Blocking Mechanism: The Proxmox firewall does not have a built-in default mechanism to block all incoming traffic until the firewall rules are applied. Ideally, a firewall should start by blocking all traffic and only allow necessary traffic once the configuration is loaded. Without this, there is a risk of exposure during network initialization.
- Vulnerability in Single Node Setups: In a single-node configuration, where there is no redundancy or external firewalls, the risk is even higher. If the cluster service fails or the firewall doesn’t start correctly, the host is left unprotected. This is particularly concerning in environments where the Proxmox host is directly exposed to the internet or other untrusted networks.
Best Practices for Securing Your Proxmox Host
Given these limitations, it is essential to implement additional layers of security to protect your Proxmox host and not rely solely on the built-in firewall. Below are some key strategies to enhance your host’s security:
1. Use External Firewalls
While the Proxmox firewall offers convenient protection, it should not be the only firewall in your setup. Implementing an external firewall — either hardware-based or another software firewall solution — can ensure that your host is protected from the moment it boots up. The external firewall should be configured to block all unnecessary traffic to your Proxmox host and limit access to management ports (e.g., SSH, web UI) to trusted IP addresses only.
2. Implement a Drop-All Default Rule
If you choose to rely on Proxmox firewall for the host zone, it’s a good idea to manually configure a drop-all rule that blocks all incoming traffic by default during boot-up. This can prevent unwanted access while the network and firewall services are initializing. Although Proxmox does not currently support this by default, configuring your own rules to drop all traffic until the full ruleset is loaded can provide some protection.
3. Monitor Cluster and Firewall Services
Regularly monitor the status of both the cluster and firewall services to ensure they are functioning correctly. Automating alerts for service failures or unusual behavior in these components can help you react quickly to any vulnerabilities.
4. Segment Your Network
Network segmentation is another effective way to protect your Proxmox host. By placing your Proxmox server in a secure, isolated network zone (e.g., a DMZ), you limit exposure to external threats. Combine this with VLANs to isolate different types of traffic (e.g., management traffic, virtual machine traffic, etc.), reducing the risk of unauthorized access.
5. Use Secure Access Methods
To minimize the risk of unauthorized access, always use secure methods to access your Proxmox server. Disable password-based SSH access and instead use SSH key authentication. Additionally, consider using a VPN or other secure tunnels to access the Proxmox management interface from external locations, rather than exposing it directly to the internet.
6. Keep Your System Updated
Regularly updating both Proxmox and its underlying operating system is critical for ensuring security. Security patches often address vulnerabilities that could be exploited by attackers. Make sure to apply updates as soon as they are available and consider using automated tools to notify you of critical patches.
7. Backup Configuration Files Regularly
In case of service failures or configuration corruption, having regular backups of your Proxmox firewall and cluster configuration files ensures that you can quickly restore the necessary settings without prolonged downtime. Automated backups will save you time and provide peace of mind.
Strengthening Your Proxmox Security
While the Proxmox firewall is a useful tool, it has several limitations that make it unwise to rely on it as the sole layer of security for your host. Its dependency on cluster services and the lack of immediate rule application during boot-up expose the host to potential risks. By implementing external firewalls, using drop-all default rules, monitoring services, and practicing secure access methods, you can significantly reduce the risk of unauthorized access and protect your Proxmox environment more effectively.
Ultimately, securing your Proxmox host requires a multi-layered approach that extends beyond the built-in firewall. Proactive measures, regular monitoring, and thoughtful network design will go a long way in ensuring the security and integrity of your virtual environment.
Reply below to know how you can achieve it with your setup.