Introduction
This guide explains how to use Tailscale as an alternative connectivity solution with Pangolin. Instead of using Newt/WireGuard tunneling provided by the Gerbil component, we’ll create a secure mesh network with Tailscale that connects your VPS to your home lab. This approach allows you to use Pangolin in “Local” mode while still maintaining secure access to your home lab resources.
Benefits of Using Tailscale with Pangolin
- Zero-config networking: Tailscale automatically handles NAT traversal and firewall issues
- End-to-end encryption: All traffic is encrypted with WireGuard (which Tailscale uses under the hood)
- Simple setup: No need to configure port forwarding or complex networking
- Single sign-on: Use existing identity providers for authentication
- MagicDNS: Automatic DNS resolution for your devices on the Tailscale network
Prerequisites
- A VPS with a public IP address running Linux (Ubuntu/Debian recommended)
- A domain name pointing to your VPS
- Root access to both your VPS and home lab machines
- Basic familiarity with the command line
- TCP ports 80 and 443 exposed on your VPS (for Pangolin/Traefik)
1. Set Up Tailscale Network
Install Tailscale on VPS
# On Ubuntu/Debian
curl -fsSL https://tailscale.com/install.sh | sh
# On RHEL/CentOS/Fedora
dnf install tailscale
sudo systemctl enable --now tailscaled
# On other distros, see: https://tailscale.com/download
Install Tailscale on Home Lab Server
# On Ubuntu/Debian
curl -fsSL https://tailscale.com/install.sh | sh
# For other platforms, see: https://tailscale.com/download
Connect Both Systems to Tailscale
On both the VPS and home lab server:
sudo tailscale up
This will provide a URL to authenticate with Tailscale. Open the URL in a browser and log in with your Tailscale account.
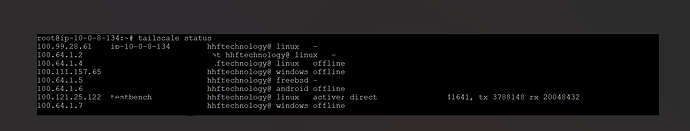
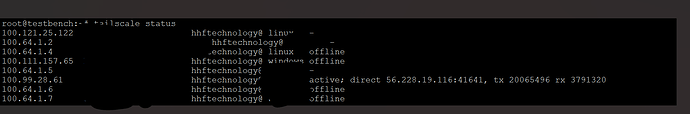
Verify Connectivity
On either machine, check the status and note the Tailscale IP addresses:
tailscale status
Example output:
100.100.100.100 vps-server user@example.com linux active -
100.100.100.101 homelab-server user@example.com linux active -
VPS
HOMELAB
Make note of your home lab server’s Tailscale IP (e.g., 100.100.100.101). You’ll need this later when configuring Pangolin.
Enable IP Forwarding on VPS
echo 'net.ipv4.ip_forward = 1' | sudo tee -a /etc/sysctl.conf
sudo sysctl -p
2. Install Pangolin on VPS without Tunneling
Since we’re using Tailscale for connectivity, we’ll install Pangolin without the Gerbil tunneling component.
Download and Run the Installer
# Download the installer
wget -O installer "https://github.com/fosrl/pangolin/releases/download/v1.1.0/installer_linux_amd64"
chmod +x ./installer
# Run the installer
sudo ./installer
Configure Pangolin Without Tunneling
During the installation:
- Enter your base domain and dashboard domain as prompted
- Provide an email for Let’s Encrypt
- When asked if you want to install Gerbil for tunneling, select No
- Configure your admin user email and password
- Set your security preferences for signups and organization creation
The installer will generate a Docker Compose file similar to this:
name: pangolin
services:
pangolin:
image: fosrl/pangolin:1.1.0
container_name: pangolin
restart: unless-stopped
volumes:
- ./config:/app/config
healthcheck:
test: ["CMD", "curl", "-f", "http://localhost:3001/api/v1/"]
interval: "3s"
timeout: "3s"
retries: 5
traefik:
image: traefik:v3.3.3
container_name: traefik
restart: unless-stopped
ports:
- 443:443
- 80:80
depends_on:
pangolin:
condition: service_healthy
command:
- --configFile=/etc/traefik/traefik_config.yml
volumes:
- ./config/traefik:/etc/traefik:ro
- ./config/letsencrypt:/letsencrypt
- ./config/traefik/logs:/var/log/traefik
networks:
default:
driver: bridge
name: pangolin
3. Configure Pangolin for Local Mode
After installation, let’s ensure the Pangolin configuration is properly set up for local mode:
Edit config/config.yml if needed:
app:
dashboard_url: "https://your-pangolin-domain.com"
base_domain: "your-domain.com"
log_level: "info"
save_logs: false
server:
external_port: 3000
internal_port: 3001
next_port: 3002
internal_hostname: "pangolin"
session_cookie_name: "p_session_token"
resource_access_token_param: "p_token"
resource_session_request_param: "p_session_request"
traefik:
cert_resolver: "letsencrypt"
http_entrypoint: "web"
https_entrypoint: "websecure"
prefer_wildcard_cert: true
# Note: gerbil section can be deleted or left as is
rate_limits:
global:
window_minutes: 1
max_requests: 100
users:
server_admin:
email: "admin@your-domain.com"
password: "YourSecurePassword123!"
flags:
require_email_verification: false
disable_signup_without_invite: true
disable_user_create_org: false
allow_raw_resources: true
allow_base_domain_resources: true
4. Start Pangolin and Access the Dashboard
sudo docker compose up -d
After the containers start, access your Pangolin dashboard at your configured URL (e.g., https://your-pangolin-domain.com).
5. Setting Up Site and Resources in Pangolin
1. Create Your Organization
After logging in with your admin credentials:
- You’ll be prompted to create an organization
- Enter a name (e.g., “Home Lab”)
- Enter an ID (e.g., “homelab”) - Note: This cannot be changed later
2. Create a Local Site
- Go to the Sites tab
- Click the Add Site button
- Give your site a name (e.g., “Home Server”)
- Select the connection method: Local
- Click Create Site
This creates a site that uses the local network (which now includes our Tailscale network).
3. Create a Resource
- Go to the Resources tab
- Click the Add Resource button
- Enter resource details:
- Name (e.g., “Home Assistant”)
- Subdomain (e.g., “homeassistant”)
- Select the site you created
- Click Create Resource
4. Configure Resource Target with Tailscale IP
- Navigate to the resource you just created
- Go to the Connectivity tab
- Add a target with the following details:
- Method: Choose HTTP or HTTPS depending on your service
- IP Address: Enter your home lab’s Tailscale IP (e.g.,
100.100.100.101) - Port: Enter the port your service runs on (e.g.,
8123for Home Assistant)
- Click Add Target
- Click Save Changes
Example configuration for Home Assistant:
- Method: HTTP
- IP Address: 100.100.100.101
- Port: 8123
5. Configure Authentication
- Navigate to the Authentication tab for your resource
- By default, the resource is protected with your Pangolin credentials (Platform SSO)
- Adjust authentication settings as needed (SSO, password, email whitelist, etc.)
6. Test Access
Once Let’s Encrypt provisions the SSL certificate (which may take a few minutes), you can access your resource at:
https://subdomain.your-domain.com
6. Additional Configuration for Multiple Services
Adding More Home Services
Repeat the “Create a Resource” and “Configure Resource Target” steps for each service you want to expose. Use the same site but different subdomains and target ports.
Example services:
- Plex Media Server (port 32400)
- Nextcloud (port 443)
- Jellyfin (port 8096)
- Bitwarden (port 8080)
Tailscale Subnet Routing (Optional)
If you have other devices on your home network that aren’t running Tailscale directly, you can enable subnet routing:
- On your home lab server, find your local subnet (e.g., 192.168.1.0/24)
- Enable subnet routing:
sudo tailscale up --advertise-routes=192.168.1.0/24
- In the Tailscale admin console, approve the subnet routes
- For Pangolin resource targets, you can now use local IPs (e.g., 192.168.1.10)
7. Troubleshooting
Connectivity Issues
If you’re having connectivity issues between your VPS and home lab:
- Check Tailscale status:
tailscale status
- Verify ping works between your devices:
ping 100.100.100.101 # Replace with your home lab's Tailscale IP
- Check that Tailscale is running on both devices:
sudo systemctl status tailscaled
Certificate Issues
If you’re having issues with SSL certificates:
- Check Traefik logs:
docker logs traefik
-
Verify that ports 80 and 443 are open on your VPS
-
Ensure your domain is correctly pointing to your VPS IP
Resource Access Issues
If you’re having trouble accessing your resources:
- Verify the Tailscale connection is active on both ends
- Check that you’re using the correct Tailscale IP in the resource target
- Ensure the service is running and accessible on the specified port
- Check Pangolin logs:
docker logs pangolin
8. Security Considerations
Tailscale ACLs
For added security, consider configuring Tailscale ACLs to restrict which devices can communicate:
- Visit the Tailscale admin console (Tailscale)
- Configure ACLs to restrict traffic as needed
Pangolin Authentication
Even though your resources are only accessible through Tailscale, it’s good practice to maintain authentication:
- Keep Platform SSO enabled for resources
- Consider using resource-specific passwords for sensitive services
- Enable email whitelisting for resources that need additional security
Conclusion
You’ve now set up a secure connection between your VPS running Pangolin and your home lab using Tailscale. This configuration allows you to expose your home services through Pangolin without using Newt or opening ports on your home network.
The main advantages of this approach:
- Simplified networking with Tailscale’s mesh VPN
- No port forwarding required on your home router
- Secure, encrypted connections between all devices
- DNS name resolution with Let’s Encrypt certificates
- Authentication and access control through Pangolin
Remember to keep both Tailscale and Pangolin updated for the latest security features and bug fixes.