Experience the advanced capabilities of CloudPanel for web server management, enhanced by the real-time security features of CrowdSec. By integrating CrowdSec with CloudPanel, users can streamline their web server administration while significantly bolstering security measures. This synergistic combination not only simplifies management tasks but also fortifies defenses against cyber threats, ensuring a robust hosting environment.
Key Features
- Seamless Integration: The integration of CrowdSec into CloudPanel allows for automated threat detection and mitigation, enhancing the overall security posture of the web server.
- User-Friendly Interface: CloudPanel offers an intuitive interface that facilitates efficient management of multiple applications, domains, and databases.
- Robust Security Framework: With CrowdSec’s real-time monitoring capabilities, users benefit from proactive defense mechanisms against various attack vectors.
Advantages
- Streamlined Management: The combined functionalities of CloudPanel and CrowdSec enable users to focus on application development rather than server maintenance.
- Enhanced Security Protocols: Utilizing CrowdSec’s community-driven threat intelligence provides an additional layer of security, adapting to emerging threats dynamically.
- Optimized Performance: The lightweight architecture of CloudPanel ensures that server resources are utilized effectively, resulting in improved application performance.
In summary, the collaboration between CloudPanel and CrowdSec empowers users to maintain high-performance web servers while ensuring comprehensive security, thus allowing developers to concentrate on delivering exceptional applications without security concerns.
Integration of CloudPanel and CrowdSec for Enhanced Web Server Management
This document outlines the integration of CloudPanel with CrowdSec, a powerful combination designed to streamline web server management while simultaneously enhancing security.
Installation Procedure
Prerequisites for CloudPanel Installation
Begin the installation process on a freshly provisioned Ubuntu 24.04 LTS server.
Steps for Installing CrowdSec
The installation of CrowdSec is a straightforward process that can be completed in three primary steps:
-
Adding the CrowdSec Repository
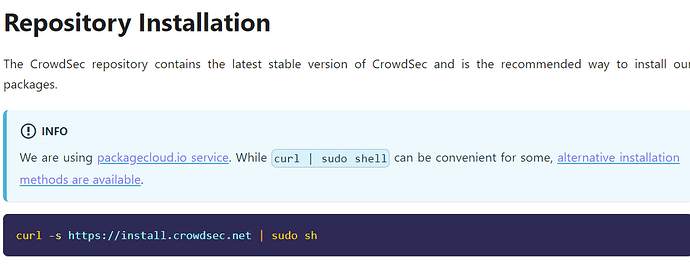
To initiate the installation, add the CrowdSec repository by executing the following command with elevated privileges:
curl -s curl -s https://install.crowdsec.net | sudo sh
-
Installing CrowdSec
After successfully adding the repository, install CrowdSec by running:
apt install crowdsec -
Installing a Firewall Bouncer
To enhance security further, install the firewall bouncer component using:
sudo apt install crowdsec-firewall-bouncer-iptables
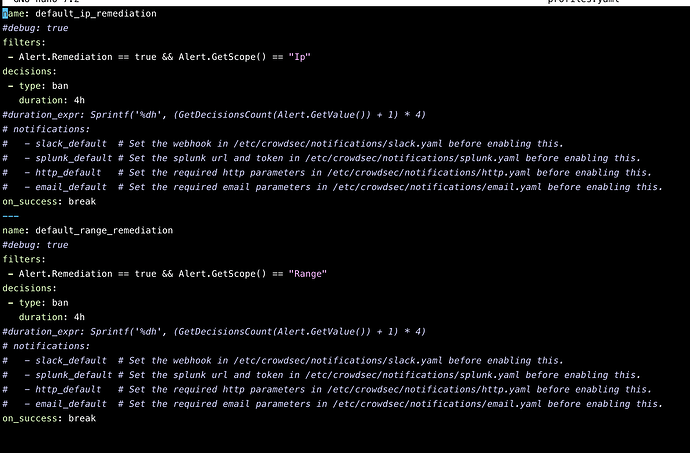
Configuration and Conflict Resolution
During the installation, users may encounter port conflict errors that could hinder the proper startup of CrowdSec. This section provides guidance on resolving such issues through configuration adjustments.
Modifying Configuration Files
To ensure optimal functionality, several configuration files require modification:
/etc/crowdsec/config.yaml/etc/crowdsec/bouncers/crowdsec-firewall-bouncer.yaml/etc/crowdsec/local_api_credentials.yaml
Steps to Modify config.yaml:
- Open your preferred text editor and access the file located at
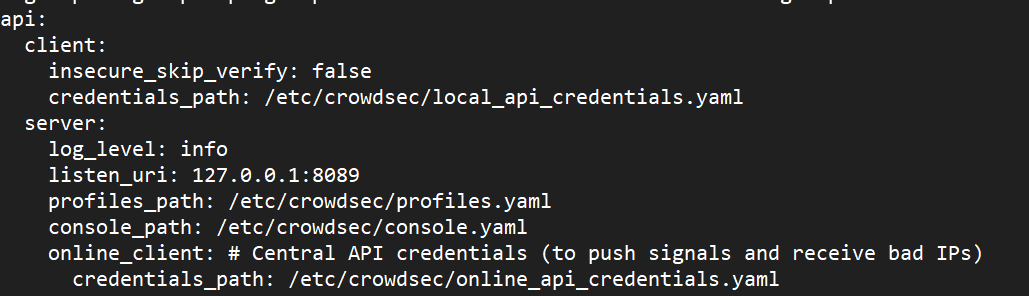
/etc/crowdsec/config.yaml. - Locate the line specifying
listen_uri: 127.0.0.1:8080. - Change this line to
listen_uri: 127.0.0.1:8089to avoid port conflicts. - Save your changes.
Your updated config.yaml should reflect this modification.
Steps to Modify crowdsec-firewall-bouncer.yaml:
- Open
/etc/crowdsec/bouncers/crowdsec-firewall-bouncer.yamlin your text editor. - Find the line
api_url: http://127.0.0.1:8080/. - Update it to
api_url: http://127.0.0.1:8089/. - Save your changes.
Your modified crowdsec-firewall-bouncer.yaml file will now be configured correctly.
Steps to Modify local_api_credentials.yaml:
- Access
/etc/crowdsec/local_api_credentials.yamlin your text editor. - Locate
url: http://127.0.0.1:8080. - Change it to
url: http://127.0.0.1:8089. - Save your changes.
The updated local_api_credentials.yaml will now be properly configured.
Restarting Services
Once all configuration files have been modified, restart the necessary services to apply changes:
systemctl restart crowdsec-firewall-bouncer
systemctl restart crowdsec
To verify that the CrowdSec service is running correctly, execute:
service crowdsec status
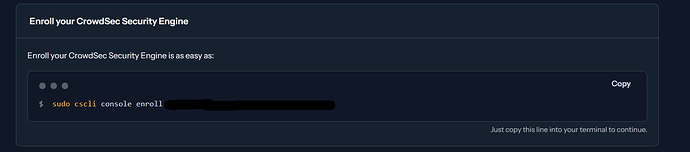
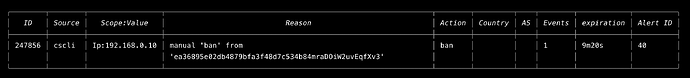
Once Installed, connect to your crowdsec dashboard, execute:
sudo cscli console enroll yourkey
remove -e context other wise it will throw up an error
any questions on how to setup nginx and other option reply to this thread.